Checkmarx has uncovered a threat actor that has been quietly infiltrating the open-source ecosystem for nearly six months, planting malicious Python packages with a focus on deception and financial gain.
The malicious actor employed a systematic approach, disguising their packages with names closely resembling popular legitimate Python packages. These decoy packages, camouflaged to blend in, successfully garnered thousands of downloads. The malicious payload, embedded within the setup.py file, executed upon installation, showcasing a level of sophistication.
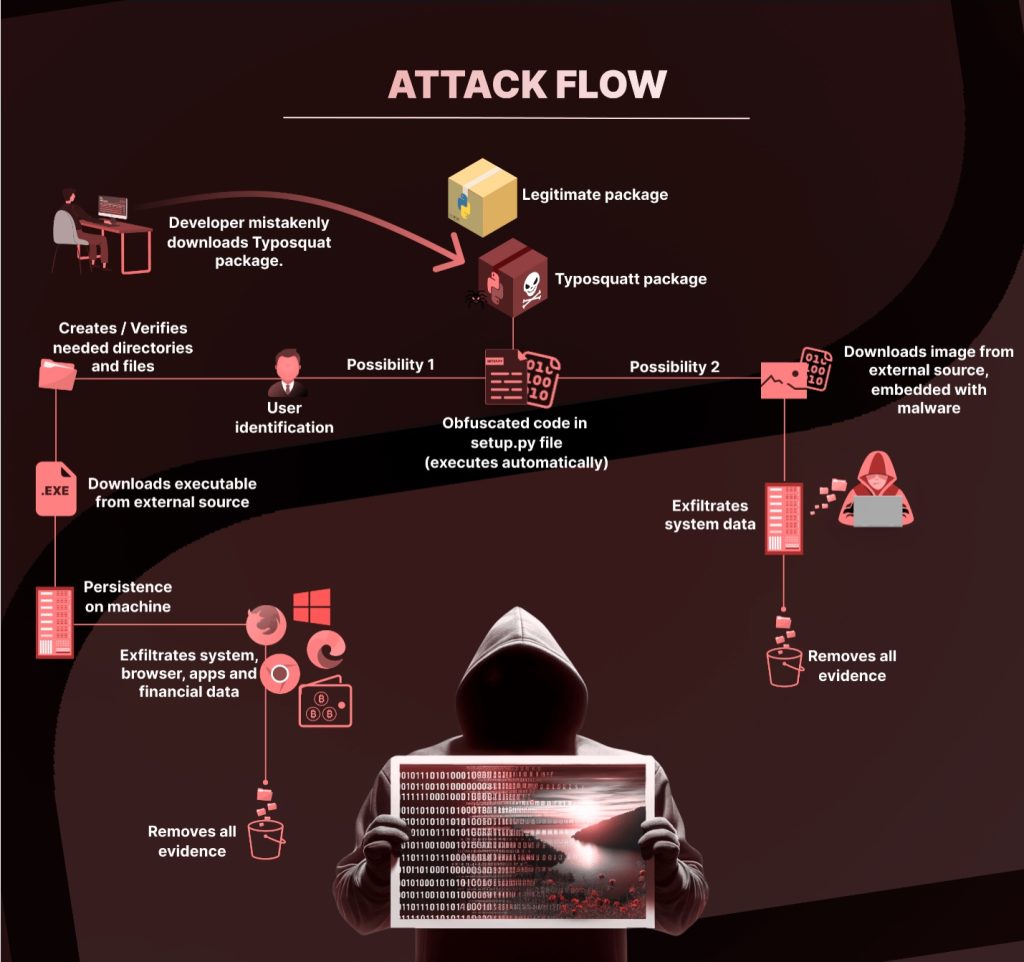
One notable aspect of the attack involved steganography, hiding a malicious payload within an innocuous-looking image file. This technique added an extra layer of stealth, making detection challenging. The attack demonstrated a consistent pattern, with code exhibiting similar obfuscation techniques and harmful payloads.
The Python packages, both camouflaged and direct, showcased a common blueprint. The attacker – aiming for persistence on compromised systems – employed scripts that identified users, created specific directories, placed and executed files, and covered their tracks post-execution.
The ultimate goal of the packages was clear: gain persistence, steal sensitive information, and achieve financial gains. The attacker targeted cryptocurrency assets, with a focus on stealing financial data. Stolen information was stored in separate files and exfiltrated to specific endpoints.
The attacker went beyond direct attacks, creating packages masquerading as API management tools. These packages – named “Pystob” and “Pywool” – enticed victims to deliberately download them, revealing obfuscated code and a multi-layered malicious payload.
To appear more legitimate, the attacker utilised the domain ‘api-hw.com’ for downloading payloads. However, the loss of control over the domain indicates a potential shift in strategy or a retreat.
The campaign uncovered by Checkmarx serves as a stark reminder of the persistent threats targeting the open-source ecosystem. Developers must exercise caution, vet packages, and leverage security assessment platforms to make informed decisions and reduce risks in their DevOps pipelines.
See also: Wallarm highlights disturbing trends in API security threats

Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with Digital Transformation Week.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.